Nation-sponsored malware with Stuxnet ties has mystery warhead
Researchers have uncovered yet another state-sponsored computer espionage operation that uses state-of-the-art software to extract a wealth of sensitive data from thousands of machines located mostly in the Middle East.
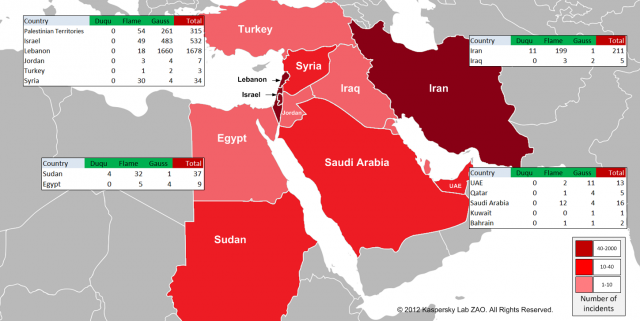
"Gauss," as Kaspersky Lab researchers have dubbed the malware, was devised by the same "factory" or "factories" responsible for the Stuxnet worm used to disrupt Iran's nuclear program, as well as the Flame and Duqu Trojans. Some researchers say the latter two malware titles may have provided the reconnaissance needed for operations such as Stuxnet. Gauss is known to have infected 2,500 computers connected to Kaspersky's cloud-based security system, and researchers with the firm say tens of thousands of additional machines may also be affected. The highest concentration of attacks are found in Lebanon, followed by Israel and the Palestinian territories.
"The discovery of Gauss indicates that there are probably many other related cyber-espionage malware in operation," Kaspersky researchers wrote in a 48-page report published Thursday morning (a condensed blog post is here). "The current tensions in the Middle East are just signs of the intensity of these ongoing cyber-war and cyber-espionage campaigns."
Like Duqu, Gauss is highly modular, and it shares a "fair deal of code" with Flame. Its developers failed to remove debugging information before unleashing the malware, however, allowing researchers to uncover details about the computers used to develop the malware. A version developed in December and January, for instance, resided in the Windows directory c:\documents and settings\flamer\desktop\gauss_white_1, providing another clue it has close ties to Flame, which is also known as Flamer and didn't come to light until May. Gauss and Flame also share a similar command and control infrastructure, code references, and encryption subroutines. Gauss, which appears to be an homage to the German mathematician and scientist Johann Carl Friedrich Gauss, comes from the name one of the developers gave to the main module. Developers appear to have named other modules after famous mathematicians and philosophers Kurt Godel and Joseph-Louis Lagrange.
http://arstechnica.com/security/2012/08/nation-sponsored-malware-has-mystery-warhead/