Stuxnet, gone rogue, hit Russian nuke plant, space station
Last edited Tue Nov 12, 2013, 02:06 AM - Edit history (1)
Source: Times of Israel
A Russian nuclear power plant was reportedly “badly infected” by the rogue Stuxnet virus, the same malware that reportedly disrupted Iran’s nuclear program several years ago. The virus then spread to the International Space Station via a Stuxnet-infected USB stick transported by Russian cosmonauts.
Speaking to journalists in Canberra, Australia, last week, Eugene Kaspersky, head of the anti-virus and cyber protection firm that bears his name, said he had been tipped off about the damage by a friend who works at the Russian plant.
Kaspersky did not say when the attacks took place, but implied that they occurred around the same time the Iranian infection was reported. He also did not comment on the impact of the infections on either the nuclear plant or the space station, but did say that the latter facility had been attacked several times.
The revelation came during a question-and-answer period after a presentation on cyber-security. The point, Kaspersky told reporters at Australia’s National Press Club last week, was that not being connected to the Internet — the public web cannot be accessed at either the nuclear plant or on the ISS — is a guarantee that systems will remain safe. The identity of the entity that released Stuxnet into the “wild” is still unknown (although media speculation insists it was developed by Israel and the United States), but those who think they can control a released virus are mistaken, Kaspersky warned. “What goes around comes around,” Kaspersky said. “Everything you do will boomerang.”
<snip>
Read more: http://www.timesofisrael.com/stuxnet-gone-rogue-hit-russian-nuke-plant-space-station/
Via https://twitter.com/NASAWatch/statuses/400063497783898112
and http://io9.com/stuxnet-has-infected-a-russian-nuclear-plant-and-the-sp-1462375259
Niceguy1
(2,467 posts)Usb ports weren't deactivated?
bananas
(27,509 posts)Stuxnet: UK and US nuclear plants at risk as malware spreads outside Russia
by Alastair Stevenson
11 Nov 2013
Security experts have warned the notorious Stuxnet malware has likely infected numerous power plants outside of Russia and Iran.
Experts from FireEye and F-Secure told V3 the nature of Stuxnet means it is likely many power plants have fallen victim to the malware, when asked about comments made by security expert Eugene Kaspersky claiming at least one Russian nuclear plant has already been infected.
<snip>
F-Secure security analyst Sean Sullivan told V3 Stuxnet's unpredictable nature means it has likely spread to other facilities outside of the plant mentioned by Kaspersky.
<snip>
Director of security strategy at FireEye, Jason Steer, mirrored Sullivan's sentiment, adding the insecure nature of most critical infrastructure systems would make them an ideal breeding ground for Stuxnet.
<snip>
"Many of these control systems are not connected to the internet, because they are so old and delicate that they cannot withstand any serious probing and examination, and frankly are not designed to connect to the internet as they are so insecure. Getting a vulnerability to a network not connected is not so difficult anymore if it's important enough."
<snip>
"It's highly likely that other plants globally are infected and will continue to be infected as it's in the wild and we will see on a weekly basis businesses trying to figure out how to secure the risk of infected USB flash drives," he said.
<snip>
Katashi_itto
(10,175 posts)delrem
(9,688 posts)Part of a rogue war.
Response to bananas (Original post)
Name removed Message auto-removed
Berlum
(7,044 posts)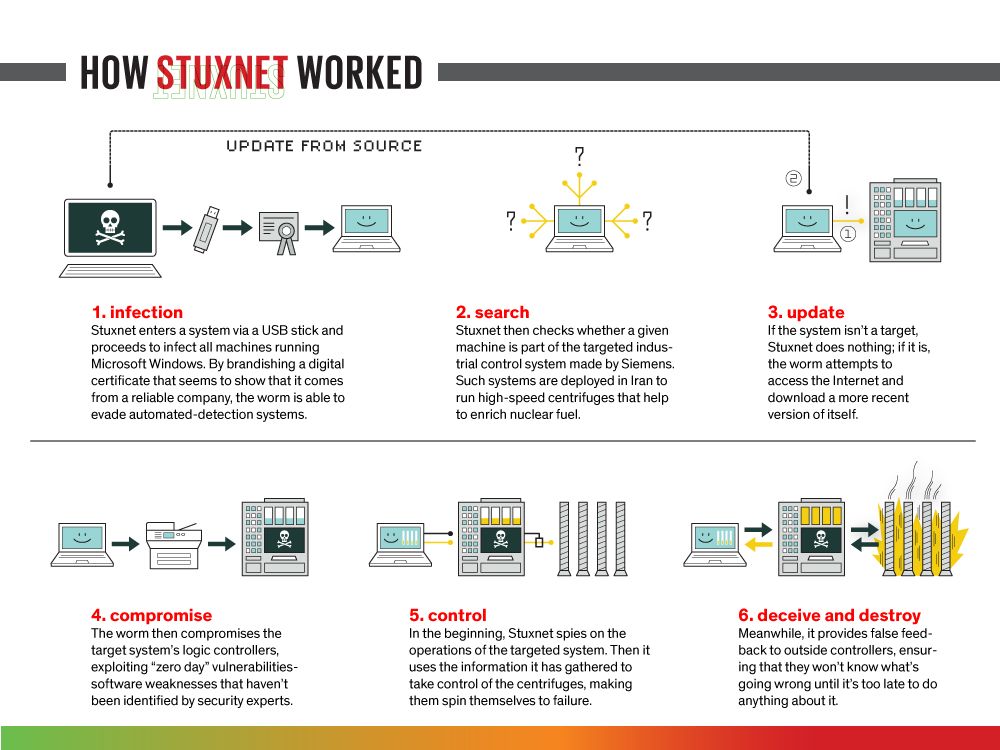
MindPilot
(12,693 posts)That's my new sig.
At my next staff meeting where co-workers are talking about air-gapping for security, I can use this--the widest air-gapping ever!--to point out that it doesn't really work.
Kelvin Mace
(17,469 posts)Like bioweapons, it WILL come back and infect things you didn't mean for it to infect.
It will be interesting to see if the corporate media covers this in the states.
L0oniX
(31,493 posts)hollowdweller
(4,229 posts)cheapdate
(3,811 posts)The source of some of these claims seems to be commercial cyber-security companies who stand to gain from publicizing risks -- even overstating or exaggerating the risk.
My understanding of the Stuxnet attack on Iran's centrifuges was that the Stuxnet code was highly specific to the Siemens control system in use at the Iranian centrifuge facility. Programming the virus to cause the process displays and monitors to falsely display normal operating parameters would have required finely detailed knowledge of the specific configuration of the centrifuge facility's control system. The Stuxnet virus was introduced with a USB flash drive and probably required a person on the inside.
The claims in this article contradict my understanding of the Stuxnet virus and contradict what has been discussed elsewhere by professional control system security experts.
I'm skeptical of this. But it's hard to separate information from misinformation.
okaawhatever
(9,461 posts)cprise
(8,445 posts)cheapdate
(3,811 posts)within the process control and automation community. It's been the subject of conferences, papers, standards committees meetings, etc.
This article from Control magazine is typical.
http://www.controlglobal.com/whitepapers/2011/006/
NickB79
(19,233 posts)It caught a different virus.
cprise
(8,445 posts)...his company and as a person. I would tend to believe him and would be more worried that the newspaper is twisting his words, if anything.
He has basically admitted that antivirus scanners are a dead-end approach to security... yet his company's main revenue stream comes from antivirus.
Response to bananas (Original post)
Name removed Message auto-removed
NickB79
(19,233 posts)At least one of them eventually got it right.
"This article originally said the ISS was infected with Stuxnet," said the Atlantic in a correction. "Upon further review of Kaspersky's statements, that's not the case. We're sorry for the confusion."
bananas
(27,509 posts)SpaceX rockets also run on linux: http://slashdot.org/story/13/03/24/2050221/spacex-lessons-learned-developing-software-for-space-vehicles